This is a walk through of what I did to resolve a capstone lab in OSCP, which focuses on finding credentials saved on a file as plain text, which can be leveraged for further escalating privileges in a system.
Required Applications
The steps listed are under the presumption that required applications are already installed and are working properly. Required applications:
- Windows VM (Provided by OffSec Lab)
- XFREERDP3 – must be installed in Kali
Steps
This is a continuation of lab about privilege escalation.
At this point, it is assumed that you are able to obtain the local Windows user steve’s password through enumerating files available in the system. When logged in as steve to the target system, try to locate the file which contains the web login password for steve.
Use this command in Powershell to search the system:
Get-ChildItem -Path C:\Users -Include *.txt,*.ini -File -Recurse -ErrorAction SilentlyContinue | Select-String -Pattern "pass" | findstr.exe steve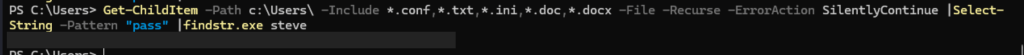
A file containing Base64-encoded string is found. I used Cyberchef to decode it to plain text. This will reveal the username and password for another user.

Using the discovered credential, run CMD as this user.

Captured Flag / Proof of Concept
