This is a walk through of what I did to resolve a capstone lab in OSCP, which focuses on Windows Privilege Escalation.
Required Applications
The steps listed are under the presumption that required applications are already installed and are working properly. Required applications:
- Kali VM
- nc
- Windows VM (Provided by OffSec Lab)
Steps
When attacking a system, the key information that must be obtained during the enumeration phase are:
- Usernames and Group Memberships
- Hostname and System Information
- IP Address and Network Information
- Installed Applications and Running Processes
Local User Enumeration
These commands can be run using cmd. To check the username of the currently logged in user:
whoamiTo determine what groups the current user is member of, use the command below. This will include the group name, SID and attributes. From the result, check which groups are notable such as Administrators, Helpdesk, Remote Desktop Users, etc.
whoami /groupsThe following commands must be run using PowerShell. This will list all local users in the system. It will also display whether the local user is enabled or disabled.
Get-LocalUserLocal Group Enumeration
This command will list all local groups in the system. The output will include the description of the group. Built-In groups in Windows OS are Administrators, Backup Operators, Remote Desktop Users (can RDP to system), Remote Management Users (can winrm to system), etc. Look for groups that can be interesting.
Get-LocalGroupGet members of local groups. This will be useful in determining who else can be local administrators or other users with other privileges.
Get-LocalGroupMember <GROUP_NAME>System Information
This command will help obtain system information such as hostname, operating system and version, platform type, domain and network information. This will also help determine whether the system is using a dynamic or a static IP address (DHCP Enabled).
systeminfoNetwork Information
Ethernet Adapter and IP Address Information
ipconfigRouting Table – look for interesting routes such as static, persistent and active routes that may be useful for lateral movement.
route printGetting all active network connections using netstat.
netstat -anoSome notable results of netstat are as follows:
- Listening to ports 80/443 means the target is a web server.
- Listening to port 3389 means it allows RDP connection.
- Established connection from a remote IP Address to port 3389 means someone is connected via RDP.
Installed Applications
Check the registry for installed applications using the PowerShell command below.
Get-ItemProperty "HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\*" | select displaynameGet-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\*" | select displaynameAside from checking the registry, enumerate the contents of Program Files folders (32 Bit and 64 Bit), C:\ Drive, Downloads folder, AppData, etc. After determining the installed applications, next step is to search for public exploits for installed application versions.
Running Processes
Run this command to get the current running processes:
Get-ProcessThis is similar to opening Task Manager in Windows. It will show what processes are currently running in the system. This will also help determine what other applications exist in the system.
Lab
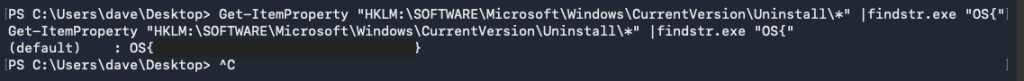
The lab for this module mentioned that the flag can be found in currently running applications. Since the result gives out a massive amount of text, I used findstr.exe to filter the result and easily find the flag.
Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\*" |findstr.exe "OS{"Captured Flag / Proof of Concept